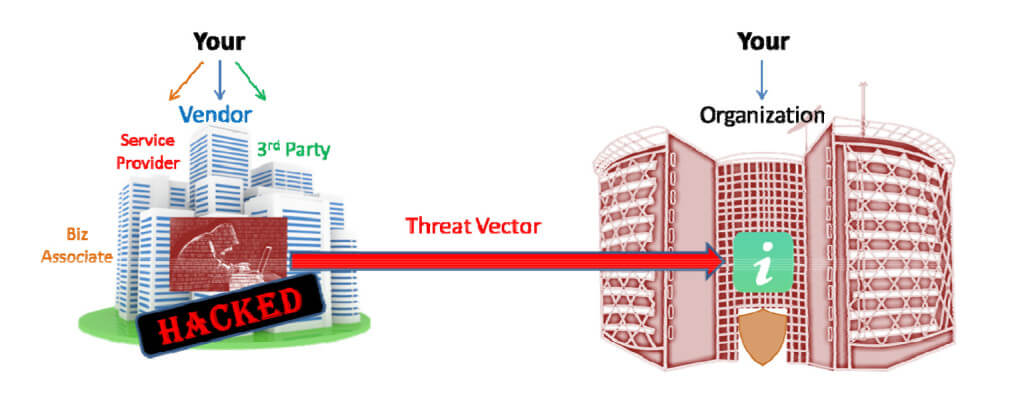
In the world of small businesses, you’re juggling multiple responsibilities, and one of the most critical is safeguarding your digital assets from cyber threats. Your choice of vendors can either bolster your defenses or introduce vulnerabilities. To navigate this complex landscape, you must conduct a vendor risk assessment.
This article is tailored to guide you through this process, addressing your unique needs and constraints as a small business owner.
Start With Clarity
Begin by understanding what matters most to your business. Is it cost-effectiveness, reliability, or top-tier security? Knowing your values and priorities will guide your vendor selection process.
Identify Your Vendors
Create an exhaustive list of all your vendors. This should encompass cloud service providers, software suppliers, consultants, and any third-party entities that have access to your systems or data.
Risk Prioritization
Not all vendors pose the same level of risk. Categorize them based on their level of access to your critical data and systems. This categorization will help you allocate resources effectively.
Understand Your Vendor’s Security
Initiate a conversation with your vendors about their security practices. Ask about the measures they have in place to protect your data and systems. Don’t hesitate to ask for documentation or audits to back up their claims.
Check for Compliance
If your industry is highly regulated, ensure that your vendors comply with the relevant standards and regulations. Non-compliance could lead to serious legal and financial consequences.
Contracts Matter
Scrutinize vendor contracts carefully. Pay special attention to clauses related to security, data protection, and liability. If necessary, consult legal expertise to ensure you’re adequately protected.
Continuous Monitoring
Cyber threats are ever-evolving. Regularly assess and monitor your vendor’s security performance. Have they kept pace with emerging threats? Regular assessments will help you identify and address vulnerabilities in a timely manner.
Penetration Testing
If feasible, consider conducting penetration tests on your vendor’s systems to uncover potential vulnerabilities. Proactive testing can reveal weaknesses that malicious actors might exploit.
Incident Response Plan
Collaborate with your vendors to establish a joint incident response plan. Ensure that everyone knows their roles and responsibilities in the event of a security breach. Having a well-coordinated response can minimize damage and downtime.
Backup Plans
Always have backup vendors in mind. In case your current vendor fails to meet your security standards or experiences an issue, having a contingency plan will keep your operations running smoothly.
Communication is Key
Maintain open communication channels with your vendors. If you notice vulnerabilities or have concerns, address them promptly. A strong partnership relies on effective communication.
Educate Your Team
Your employees are your first line of defense. Educate them on how to identify and report potential risks associated with vendors. Encourage them to stay vigilant and report any suspicious activities promptly.
Use Technology
Small businesses can benefit from vendor risk assessment tools and software designed to simplify the process. These tools can help you manage your assessments more efficiently, keeping you organized and in control.
Budget Wisely
Recognize the budget constraints of small businesses. Allocate resources wisely and make cybersecurity a priority in your financial planning. Consider it an investment in the long-term security of your business.
