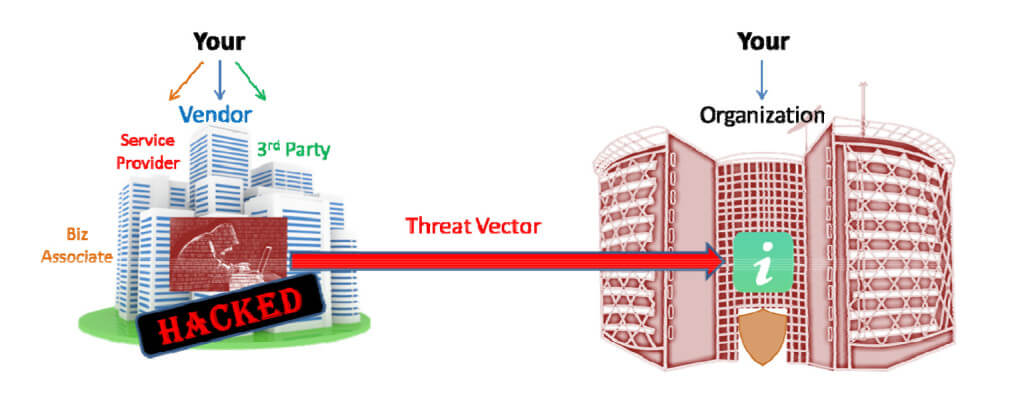
Third-party vendors have become crucial assets to businesses and are now key in carrying out their everyday operations. However, this has led to cybercriminals targeting vendors to gain access to sensitive information of the companies they work for and exploit that data.
With an enormous surge in attacks occurring since the pandemic began, organizations must ensure that vendors are reliable and that by hiring them, their data will not be at a significant risk of being stolen.
To ensure that vendors can be trusted with the company’s details, a thorough due diligence process must be carried out, which can identify both the risks attached to recruiting said vendor and how to take steps to minimize these risks.
How is vendor due diligence conducted?
Vendor due diligence varies from company to company, depending on that specific organization’s policy. The general method, however, involves sending vendors a substantial series of questions that allow the business to know the vendor and their risks while also seeing if the vendor is a good fit for the organization. The purpose of due diligence is to identify and address all potential problems associated with a vendor so that costs and contracts can be established and altered as required.
Most Effective Vendor Due Diligence Practices
As explained previously, the due diligence process will vary from each company according to their needs. The best practices when evaluating a vendor are stated below:
Collect Business Information
Firstly you should have all the information of the vendor at your disposal. This includes, but is not limited to, their proof of legitimacy, business history, standard of operations, and whether their way of conducting operations is compliant with the company’s requirements. This step will also help assess their employees’ performances, methods, and understanding of cybersecurity protocols.
Review financial information
Before getting into business with said vendor, ensure that the business’ financials are adequate and information is updated regarding all licensing fees and taxes. A company’s financial statements can help evaluate potential costs for recruiting vendors in the future.
Note operational risks
Make a list of all risks that face the organization if the vendor becomes a victim of a data breach. This will allow the business to plan ahead and be prepared to mitigate the damages should they be compromised as a result of a third-party vendor breach. ‘This disaster preparedness plan’ will highlight the strategy a company will adopt in the worst-case scenario and how they will continue operating during a data breach while also ensuring transparency and communication with relevant parties.
Assess legal risk
At times certain vendors will have access to information provided by you about your organization, customers, and personnel. Thus, the organization needs to evaluate the legal risk they will be liable for if the vendor suffers from a data breach that leaks sensitive information. Ensure your company maintains compliance and is informed of all potential legal risks before hiring a third-party vendor.
Evaluate cybersecurity risk
If you are informed of all potential cyber risks from clients, vendors, and the company, then threats can be identified and weakened before an attack happens. The company should assess the vendor’s cybersecurity stance, knowledge, and security protocols before getting into a business relationship with them.
Prioritize risk profiles
Vendors’ risk profiles should be maintained according to the amount and importance of the sensitive data being shared with them. This will help the organization be informed about which vendors to look out for and which potential problems need to be addressed first.
Continuously monitor vendor risk
Consistently monitor the potential risk associated with your vendor as the environment and technology are ever-changing, leading to new problems and increased attention required to update cybersecurity. Thus, it is crucial to assess vendors and how they adapt their cybersecurity to new threats.
Automate the questionnaire process
The questionnaire process of due diligence can be time-consuming and costly for the business, so it would be wise to install an effective third-party risk management software that can automatically send questions to vendors and evaluate whether or not, based on their answers, they would be a good fit for the business.
