In this era of relentless cyber threats, safeguarding your organization's sensitive information isn't just a priority; it's a mandate. Enter ISO 27001 – the beacon of cyber security governance that not only stands as a testament to your commitment to safeguarding digital assets but also acts as the cornerstone of an impenetrable fortress against the myriad threats lurking in the digital … [Read more...] about ISO 27001: Unraveling the Layers of Cyber Security Governance
Blog
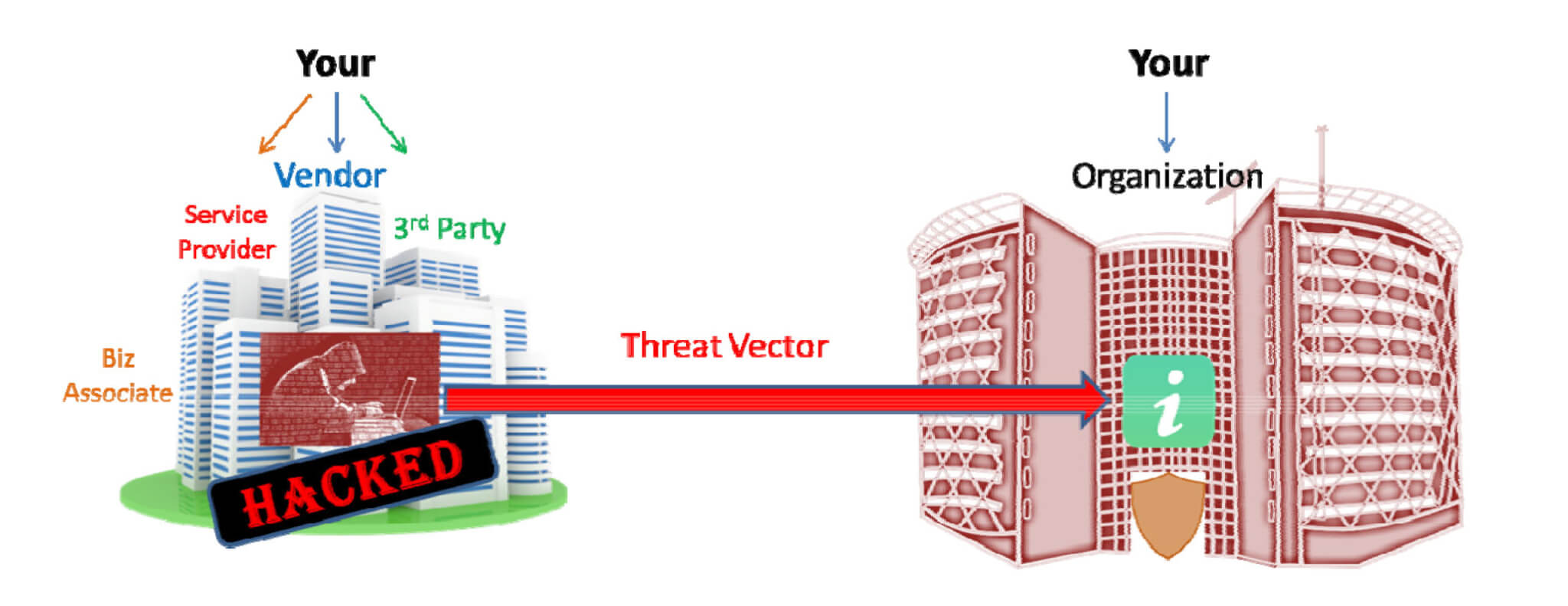
Navigating Vendor Risks: The Key Role of Certified Third-Party Risk Professionals
In today's interconnected business world, where external partnerships are the norm, the need to manage and mitigate risks associated with vendors has never been more critical. From cybersecurity vulnerabilities to compliance challenges, organizations face a myriad of risks that can impact their operations and reputation. This is where Certified Third-Party Risk Professionals (CTPRP) step … [Read more...] about Navigating Vendor Risks: The Key Role of Certified Third-Party Risk Professionals
API Security Testing
API testing and discovery tools have become increasingly vital in the development and maintenance of modern applications. With the growing reliance on APIs as a crucial component of application functionality, it is essential to thoroughly test and validate their behavior. Traditional AST toolsets may not provide comprehensive API testing capabilities, leading to the emergence of specialized tools … [Read more...] about API Security Testing
3,500 Arrested in Global Operation HAECHI-IV Targeting Financial Criminals
A six-month-long international police operation codenamed HAECHI-IV has resulted in the arrests of nearly 3,500 individuals and seizures worth $300 million across 34 countries. The exercise, which took place from July through December 2023, took aim at various types of financial crimes such as voice phishing, romance scams, online sextortion, investment fraud, money laundering … [Read more...] about 3,500 Arrested in Global Operation HAECHI-IV Targeting Financial Criminals
How to Implement HIPAA Security Controls in Office 365
To effectively implement HIPAA security controls in your Office 365 environment, it is crucial to follow a step-by-step approach. By doing so, you can enhance the security of your Office 365 environment and ensure compliance with HIPAA security controls. Let's dive into the detailed process: By following these comprehensive steps, you can establish a robust security framework for your Office … [Read more...] about How to Implement HIPAA Security Controls in Office 365