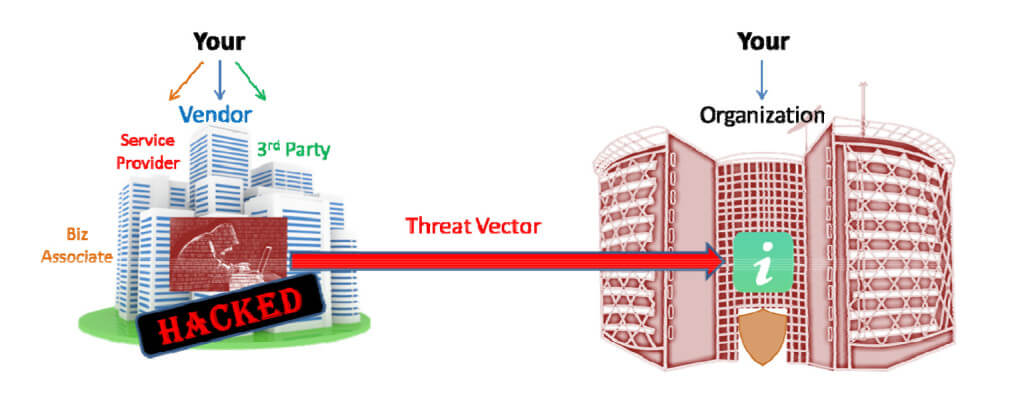
Cyber risk management is a rather challenging feat, even for the most experienced cybersecurity teams. Many day-to-day business functions depend on outsourcing to third-party companies to create a vast digital trail that ultimately requires cyber protection and monitoring. Therefore, relationship management is essential for managing cybersecurity risks in the supply chain or the vendor network.
Growth in outsourced IT signals increased risk
The Software as a Service (SaaS) model has presented new cybersecurity challenges for businesses after witnessing a dramatic increase in growth. As per the Harvey Nash/KPMG 2018 CIO Survey, approximately 75% of the survey respondents reported a moderate or significant investment in cloud infrastructure.
Critical business services, including finance, billing, human resources, enterprise resource planning (ERP), and customer relationship management (CRM), are already being outsourced by many businesses. Although convenient, outsourcing complicates vendor risk management by introducing networks that the business does not own.
Therefore, in order to manage your vendor supply chain, it is critical to establish a vendor risk management program that integrates metrics for vendor performance.
Shortage of experienced cybersecurity staff contributes to increased risk
Businesses require a team of qualified cybersecurity personnel to control information security. The supply of qualified individuals, however, has been unable to keep up with the demand, as noted by the National Institute of Standards and Technologies (NIST) in 2018.
Moreover, the lack of cybersecurity staff predicts the widening of the current skill gap. The cybersecurity skill gap and the rising complexities of third-party partner companies enable vendor management to become a constantly evolving process.
Four vendor risk management best practices
1. Risk Assessment of Individual Vendors
Every vendor provides you with a unique service to enable your business. Categorize your vendors to determine the ones that pose the highest risk, depending on the systems and the information they can access. Vendors, however, come with third parties. Therefore, you must assess individual vendors as per their supply chain associated risk.
2. Define Vendor Performance Metrics
If you are considering entering a long-term relationship with a vendor, you must define the key performance indicators (KPIs) that govern the relationship. Vendor IT’s are crucial since your vendor’s risks are directly related to you. Defining KPIs for product delivery is easy, unlike defining them for cybersecurity, which is complex.
3. Create Clear Vendor Contracts
Define your risk tolerance in your contracts. Define metrics for terminating the relationship with the help of the KPIs you establish. If your vendor does not promise security after the contract signing, you must figure out a way that keeps you protected.
4. Establish a Clear Line of Communication
It is critical to establish a clear line of communication down your supply chain. A fourth-party data breach may run your business to the ground and leave you responsible for any stolen customer information.
