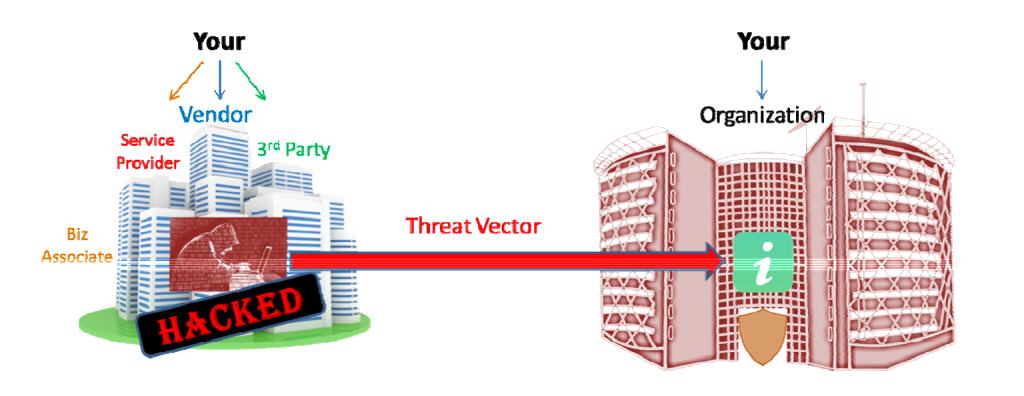
Supply chain cyber-attacks usually target the organisation’s vulnerabilities in the supply chain, including sensitive information about business partners, software providers, web developers, risk managers etc.
The supply chain is an essential part of a business. Thus, it sometimes holds confidential information, which makes it the target of cybercriminals and hackers. Recent reports suggest that up to 50% of all cyber-attacks now target the supply chain. Any business sector could be the victim of a supply chain cyberattack. The most common industries that have experienced such attacks are finance, oil & gas, and governmental institutions.
Why there is a rise in supply chain cyber attacks?
There has been a rise in the number of security breaches on many global brands recently including, Adobe, Canva, LinkedIn, Microsoft, and many government departments. These companies have initiated rigorous security measures to protect their data. With the increased security to prevent any safety violation, hackers and cybercriminals have had to find new ways to gain access. Unfortunately, the supply chain is usually the weak link in the security chain and has therefore been the source for the increased centre of attacks.
Cybercriminals can enter into the systems and breach security in the supply chain networks. In most cases, the first attack can ultimately lead to lateral attacks across many other networks globally.
There could be many reasons for offenders to break into the system smoothly, and a few of them are as follows.
- Poor cyber hygiene
Companies that have moved towards online platforms tend to experience poor cyber hygiene. It includes the use of weak passwords, a lack of security protocols and backup plans.
A report by SecureAUTH suggests that up to 53% of people use the same password across multiple platforms. Advanced hacking attacks have also been used in the past to compromise Facebook and PayPal accounts.
Once this data is available online, it becomes easier for cybercriminals to access more sensitive accounts and databases, allowing for a much more extensive supply chain attack.
Lack of training, processes and security culture are the essential factors that lead to successful attacks of this kind.
- Subcontractor vulnerabilities
Using weak software can also be the reason for application vulnerabilities, making it easier for cybercriminals to attempt and succeed in complicated attacks. Companies that outsourced their work to cheaper organisations to cut costs have experienced more application vulnerabilities.
These companies unknowingly are compromising on important information in their supply chain network to save time and money. The management should make sure that they outsource to companies that follow the same strict security guidelines as your company to prevent potential information theft.
- Malware
Malware is malicious software and code installed in authorised updates and apps to publish them as a secure application. This software can be spyware, ransomware, control and command.
Malware supply chain attacks are particularly troublesome due to the wide-ranging amount of potential victims. One of the most recent attacks has been the SolarWinds attack that was exposed in late 2020.
It is usually pretty hard to detect malware supply chain attacks since it is disguised within legitimate apps and updates. These attacks can be harmful to businesses and institutions if they lose valuable personal and financial data.
- Insider threats or user errors
Insider attacks are rare, and the motives behind such attacks are often unknown. But, Financial gain & information theft from any governmental institute is the most likely cause of such events.
For government institutions, it is necessary to conduct strict background checks on employees. Moreover, keeping employees under surveillance usually helps determine whether the attacker was one of the employees or not.
User error can be as simple as clicking on the wrong link within an email but, it could initiate a cyber-attack. Therefore, Training and guidance on dealing with similar situations are important for the company’s cybersecurity.
- Missing Encryption
Companies aim to secure their data from one network to another. Mutual trust is between suppliers, institutions, and their end-users, through encryption.Poor encryption software and the use of open-source software has led to a network of threat areas that hackers and cybercriminals can use.
Therefore, software should be encrypted strongly before installation to avoid any potential hacking attack.
Tips to protect your business from supply chain attacks
The access points used by cybercriminals and hackers to gain entry into a supply chain varies. However, far-reaching lateral attacks are a serious matter because even a single loophole can generate countless information leaks in the supply chain.
It is hard to monitor all aspects of your supply chain, especially for large corporations and institutions. But, there are numerous best practices that your institutions can follow to prevent such attacks from happening.
Vet third-party suppliers – If you are using third-party suppliers’ vet their systems and the subcontractors. It’s better to restrict access until you are satisfied with their security protocols and guidelines.
Conduct regular security and information audits – Attackers typically want data from your systems. It is advised to know where and how your data is stored can protect you from cyberattacks.
Security validation audits such as Celerity’s Cyber Threat Insight Service enable companies to understand and recognise potential vulnerabilities in their system by conducting real-world simulated cyber-attacks across your system. It lets the companies identify the gaps in their security and fix those areas before cybercriminals can exploit them.
Employee training and threat analysis – One of the simplest and most proactive methods for supply chain threat analysis is training and education of employees.
If employees notice suspicious activity and know how to respond to it, they can stop potential attacks before they go any further. Professional and regular insights can also reduce cyber threats within your company.
Early Threat Detection – Detecting a potential threat is important because it significantly reduces the amount of damage a hacker could cause to your systems. Implementing a SIEM solution provides complete visibility of your networks and can flag any for immediate action.
Better yet, a Managed SIEM can offload the resource and skills needed to manage this solution, allowing your IT team to concentrate on the core objectives.
Conclusion
As organisations improve their cybersecurity, hackers and criminals will look for backdoor access through the supply chain network. These attacks are likely to continue. Therefore, institutions need to take a proactive approach to mitigate these risks.
