
SYSTEM & ORGANIZATION CONTROLS (SOC) & SOC FOR CYBER SECURITY COMPLIANCE
System & Organization Controls (SOC) &
SOC for Cyber Security Compliance
SOC Compliance is an independent security Audit and Certification Report that allows a service organization to provide assurance and demonstrate to its customers, partners, and stakeholders that the service is being provided in a secure and reliable manner.

System & Organization Controls (SOC)
WHAT IS SOC 2?
SOC 2 is Examination and Reporting on Controls at a Service Organization
Relevant to
Security, Availability, Processing Integrity of a System,
and
Confidentiality or Privacy of the Information Processed by the System
WHY SOC 2?
With the proliferation of data breaches and hacks that occur today, there is a greater focus on information security.
With the proliferation of data breaches and hacks that occur today, there is a greater focus on information security.
While outsourcing and cloud computing can increase revenues, expand market opportunities, increase efficiency, and reduce costs for the user entities, they also result in additional risks arising from interactions with the service organization and its system.
These risks can impact finances, operations, customers, reputations, and internal controls.
Stakeholders Concerns
(Customers, Prospects, Biz Partners, BOD, executive management, government, and investors)
How the service organization can be trusted with customers’ information and that the information is secure with them?
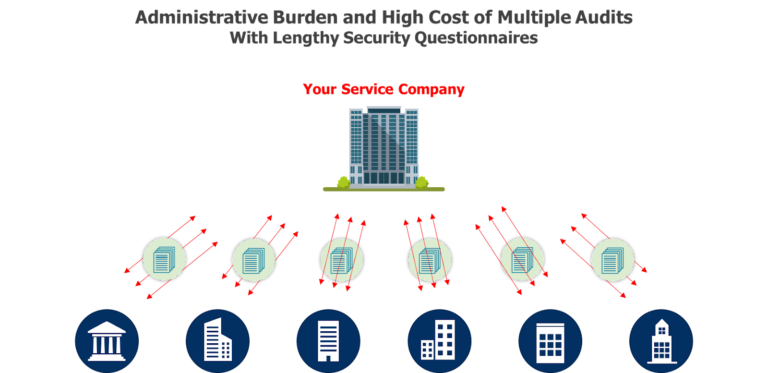
Service Providers Challenges
How to build TRUST with Customers & Business Partners
Solutions
Demonstrating Information Security at the Service Organizations and communicating with Interested Parties via SOC 2 Certification Report.

WHO ARE THE INTENDED USERS OF A SOC 2 CERTIFICATION REPORT?
Service organizations li006Be SaaS companies that process or store sensitive data for their clients, receive SOC 2 Certification Report.

Stakeholders such as customers, regulators, business partners, suppliers, and the BOD of the user organization also need SOC 2 Certification Report to ensure that there is some level of protection for their data.
WHAT ARE THE BENEFITS OF SOC 2?
SOC 2 Certification
- It is a key differentiator,provids a competitive advantage in the marketplace and expanding market opportunities
- Allows you to enter markets where a SOC 2 is a pre-requisite
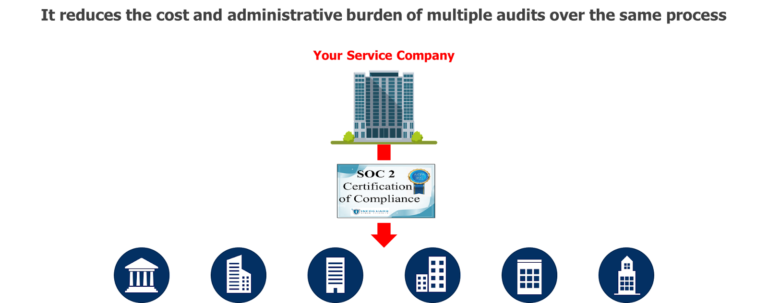
- It can save time, money, and difficulty. Reduces the cost and administrative burden of multiple audits over the same process
With SOC 2, Do it Once and Use it Many Times
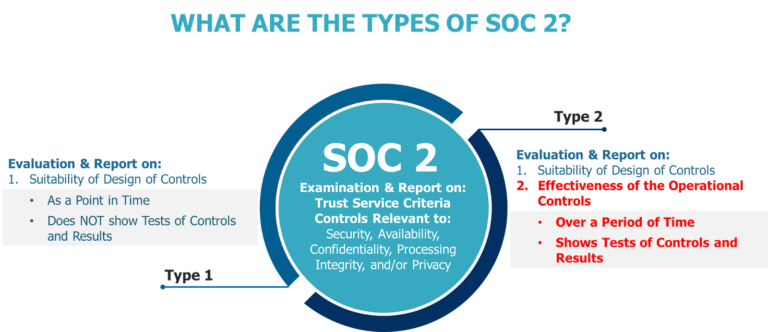
SOC 2 FOR SERVICE ORGANIZATIONS
VS.
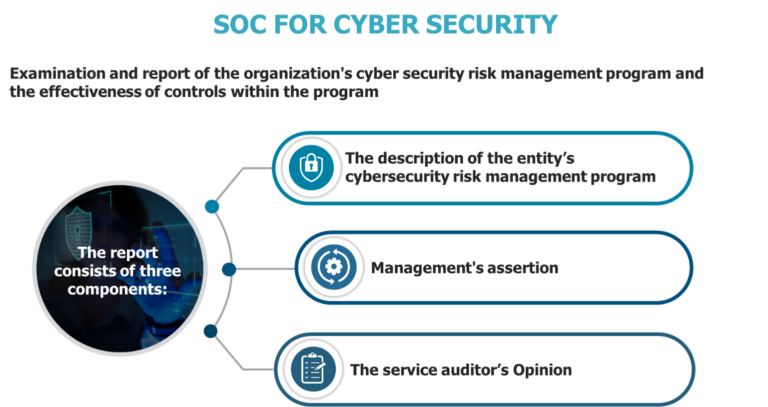
SOC FOR CYBER SECURITY


| SOC 2 for Service Organizations | SOC for Cybersecurity | |
| Purpose: | To provide information about controls at the service organization relevant to Security, availability, processing integrity, confidentiality, or privacy | To provide general users with Information about an entity’s cybersecurity risk management program and demonstrate the organization’s cyber security maturity |
| Scope: | Scoped to a specific service organization, a business unit within the service organization, or a specific service line(s). | Entire Cyber Security Risk Management Program for an organization |
| Subject of the assertion and Examination: | The description of the service organization’s system based on the description criteria | The description of the entity’s cybersecurity risk management program based on the description criteria |
| The suitability of design and operating effectiveness of the applicable trust services criteria relevant to Security, availability, confidentiality, and privacy | The effectiveness of controls within the cybersecurity risk management program to achieve the entity’s cybersecurity objectives based on the control criteria | |
| Baseline and Standards for Implementation and Evaluation: | Limited to the Trust Service Criteria (note the 2017 TSC is aligned to COSO) | Can rely on any major security framework (ISO/NIST)Can leverage the existing framework |
| Responsible Party: | Service organization management | Management of an entity |
| Third-party risk: | Can carve out sub-service organizations but must communicate due diligence and vendor management processes in place | Must be addressed in the report. It cannot be carved out.If a third party has access to company data, it must be included in the report |
| Inclusion of Sensitive Information: | The Controls Matrix is included in the report and may include sensitive Information (thus a restricted report) | Does not include the Controls Matrix section because this is very sensitive; audit work is completed but not included in the report |
| Distribution: | Restricted distribution | General distribution |
